Author: Team VB News |
Read Time: 5 Minute Read |
Audio Report Available: NO |
Video of Report: NO |
Report Language: Hindi | |
© Vishesh Baat |
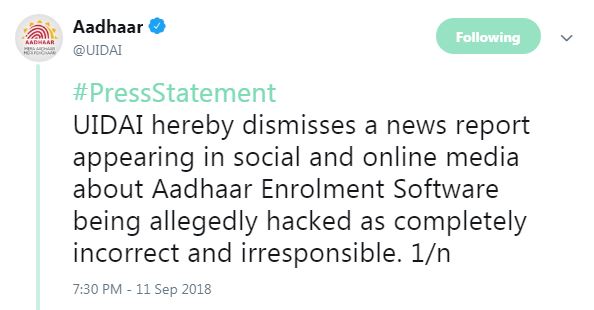
The Unique Identification Authority of India UIDAI has dismissed a news report appearing in social & online media about Aadhaar Enrolment Software being allegedly hacked as completely incorrect and irresponsible. The UIDAI has reportedly said that the claims ‘
lack substance and are baseless’.
Notably, on Tuesday there were reports in the media and social media suggesting a breach, hack in the Aadhaar software and exposure of criticial information of the citizens. However, the UIDAI then came forward, examined the matter and then dismissed all the reports of a breach.
In a press statement UIDAI said that
UIDAI hereby dismisses a news report appearing in social and online media about Aadhaar Enrolment Software being allegedly hacked as completely incorrect and irresponsible.
The series of tweets (total 24) made by UIDAI while dismissing the report of a breach in aadhaar software
The claims lack substance and are baseless. UIDAI further said that certain vested interests are deliberately trying to create confusion in the minds of people which is completely unwarranted.
Claims made in the report about Aadhaar being vulnerable to tampering leading to ghost entries in Aadhaar database by purportedly bypassing operators’ biometric authentication to generate multiple Aadhaar cards is totally baseless. 3/n
The report itself accepts that “it (patch) doesn’t seek to access information stored in the Aadhaar database”. 4/n
Its further claim “to introduce information” into Aadhaar database is completely unfounded as UIDAI matches all the biometric (10 fingerprints and both iris) of a resident enrolling for Aadhaar with the biometrics of all Aadhaar holders before issuing an Aadhaar. 5/n
All necessary safeguard measures are taken spanning from providing standardized software that encrypts entire data even before saving to any disk, protecting data using tamper proofing, identifying every one of the operators in “every” enrolment…. 6/n
….identifying every one of thousands of machines using a unique machine registration process, which ensures every encrypted packet is tracked. 7/n
Full measures are taken to ensure end-to-end security of resident data, spanning from full encryption of resident data at the time of capture, tamper resistance, physical security, access control, network security, stringent audit mechanism…. 8/n
…24×7 security and fraud management system monitoring, and measures such as data partitioning and data encryption within UIDAI controlled data centres. 9/n
It is further clarified that no operator can make or update Aadhaar unless resident himself give his biometric. 10/n
Any enrolment or update request is processed only after biometrics of the operator is authenticated and resident’s biometrics is de-duplicated at the backend of UIDAI system. 11/n
As part of our stringent enrolment & updation process, UIDAI checks enrolment operator’s biometric and other parameters before processing of the enrolment or updates and only after all checks are found to be successful, enrolment or update of resident is further processed. 12/n
Therefore it is not possible to introduce ghost entries into Aadhaar database. 13/n
Even in a hypothetical situation where by some manipulative attempt, essential parameters such as operator’s biometrics or resident’s biometrics are not captured, blurred and such a ghost enrolment/update packet is sent to UIDAI… 14/n
….the same is identified by the robust backend system of UIDAI, and all such enrolment packets get rejected and no Aadhaar is generated. 15/n
Also, the concerned enrolment machines and the operators are identified, blocked and blacklisted permanently from the UIDAI system. In appropriate cases, police complaints are also filed for such fraudulent attempts. 16/n
Similar allegations were also made before the Hon’ble Supreme Court during hearing of the Aadhaar case before the Constitution Bench which were then adequately responded by the UIDAI in the Hon’ble Supreme Court. 17/n
The reported claim of “anybody is able to create an entry into Aadhaar database, then the person can create multiple Aadhaar cards” is completely false. Some of the checks include biometric check of operator, validity of operator, enrolment machine,… 18/n
…enrolment agency, registrar, etc. which are verified at UIDAI’s backend system before further processing. In cases where, any of the checks fails, the enrolment request gets rejected & therefore any claim of creating multiple Aadhaar & compromising the database is false 19/n
If an operator is found violating UIDAI’s strict enrolment and update processes or if one indulges in any type of fraudulent or corrupt practices, UIDAI blocks and blacklists them and imposes financial penalty upto Rs.1 lakh per instance. 20/n
It is because of this stringent and robust system that as on date more that 50,000 operators have been blacklisted, UIDAI added. 21/n
We keep adding new security features in our system as required from time-to-time to thwart new security threats by unscrupulous elements. 22/n
People are also advised to approach only the authorized Aadhaar enrolment centres in bank branches, post offices and Government offices for their enrolment/updation… 23/n
…so that their enrolment/updation is done only on authorized machines and their efforts do not get wasted because of rejection of their enrolments or updates . (The list of authorized Aadhaar Kendra is available on UIDAI website http://www.uidai.gov.in ).
##### 24/24


